The notion of a “castle” is often used to illustrate the approach of traditional network security. The idea here is to build strong, towering walls, a deep, treacherous moat, and one, well-protected entrance. This would deter or, at the very least, slow down the adversaries enough that you could mount a suitable defense.
VPN (Virtual Private Networks) technology was born out of this kind of thinking. A strong wall encircles the network, and the VPN serves as the guarded entrance, allowing for secure communication and access. But as businesses shift towards the cloud and remote work becomes prevalent, the weaknesses of the “castle” approach have begun to show. Enter Software-defined Perimeter or SDP, an alternative approach to network security that is gathering momentum.
Dissecting the SDP: A Stealthy Guard for Your Network
Think of a Software-defined Perimeter as a highly-trained security guard who only allows authorized individuals into the network while remaining completely invisible to the outside world. It’s essentially a cloaking device for your servers and infrastructure.
The objective of an SDP is to conceal your on-premises or cloud-hosted infrastructure, such as servers and routers, from external parties and potential attackers. Instead of deploying a physical network perimeter, it establishes a software-based one, a far more versatile and adaptable solution.
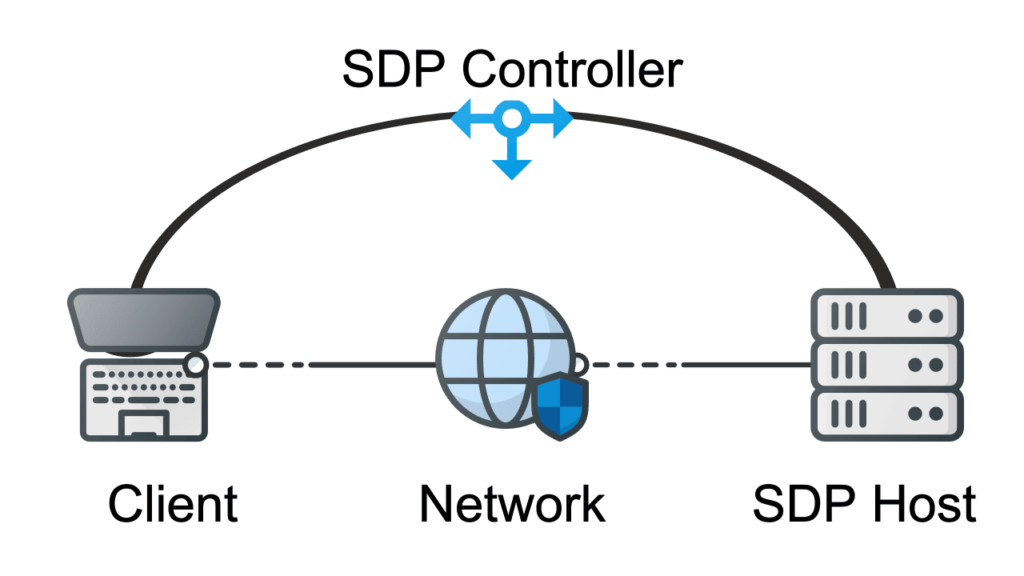
Key Components of an SDP:
- Controllers: The security managers of the system, these ensure devices are compatible with the network and manage access configurations. They mediate interactions among users, authentication providers, and protected resources.
- Clients/Users: These are the entities that seek access to network gateways remotely. They establish a secure network connection by requesting entry and authenticating themselves, creating a VPN-style tunnel to gateways.
- Gateways: The gateways include servers, data centers, and other cloud resources that need protection from unauthorized access. In an SDP deployment, access to these resources can be limited based on a “need to know” principle.
- Authentication providers: These ensure that user authentication data is provided, especially in the case of Multi-Factor Authentication. They work with the SDP controller to manage which users can utilize which gateways.
Thanks to the encryption used, all communications within this system are hidden from view and nearly impossible to intercept. The network-neutral program is flexible enough to work in a wide range of environments, scaling up quickly and easily.
VPN: A Trusted Shield for Secure Connections
A VPN creates an encrypted tunnel for data traffic over a public network, which guarantees a high degree of privacy and security. It confirms the identities of remote users and then forms an encrypted path to the internal network. This path allows you to monitor network activities and gain access to protected resources.
But how does it ensure privacy? By cloaking the user’s true identity and granting them a new one. Assuming the VPN employs robust encryption, this effectively hides their true location, the type of device they’re using, and the content of their data transfers. As a result, ISPs and other third parties won’t be able to track the websites you visit or the data you transmit and receive.
However, VPN usage isn’t without its challenges. Users may experience difficulties connecting to websites and other online services when their IP addresses are added to blocklists. Also, there’s the potential for network slowdowns and privacy concerns.
The Face-off: SDP vs. VPN
While both SDP and VPN offer secure communication, they have their own unique strengths and weaknesses. Let’s explore these further:
Advantages of Using SDP:
- Widespread device compatibility: SDP secures connections for any device that requires credentialing
- Reduction of Attack Surface: By concealing the infrastructure from the public internet, SDP significantly reduces the attack surface. Only authenticated users can see and interact with resources, reducing the risk of attacks like DDoS.
- Granular Access Control: SDP provides detailed access control policies, enabling users to access only the specific services they need. This reduces the potential damage in case of a breach.
- Scalability: Being software-based, SDPs can easily scale up or down based on the size and needs of your organization, making it suitable for businesses of all sizes.
Disadvantages of Using SDP:
- Implementation Complexity: SDP requires substantial understanding and knowledge to deploy correctly, making it a more complex solution to set up than traditional VPNs.
- Cost: Given its sophistication, SDP solutions may be more expensive than traditional VPNs. However, the total cost of ownership might balance out considering reduced risk and potential for loss.
Advantages of Using VPN:
- Established Technology: VPNs have been around for decades and are a proven solution for secure remote access.
- Cost-Effective: Since VPN technology is mature and widespread, it tends to be less expensive than newer alternatives like SDP.
- Privacy: VPNs not only provide security but also privacy. They mask the user’s actual IP address, making it difficult for third parties to track their online activities.
Disadvantages of Using VPN:
- Limited Scalability: VPNs might not be the best fit for businesses with a large number of remote workers or extensive cloud resources due to limitations in scalability and performance.
- Security Risks: VPNs expose the entire internal network once access is granted, which could be a potential risk if a user’s credentials are compromised.
- Performance Issues: Encrypted VPN tunnels may cause a slowdown in network performance, especially for users in geographically distant locations.
In conclusion, the choice between an SDP and a VPN depends on your specific use case, resources, and security needs. While SDPs provide superior security and granular control, they may be more complex and expensive to implement. On the other hand, VPNs offer a simpler, cost-effective solution but may come with potential security risks and performance issues. The best approach is to conduct a thorough analysis of your requirements, then choose the solution that aligns best with your business objectives.




