In an era where remote work has become a norm, enterprises are constantly exploring ways to extend corporate security to workers’ personal environments. One solution rapidly gaining attention is the VPN concentrator. This robust tool allows employees to securely access a company’s internal network from virtually anywhere in the world. But, what exactly is a VPN (Virtual Private Network) concentrator? How does it function? What are its benefits, and when should you use it? This comprehensive article will guide you through these questions.
Delving Into the World of VPN Concentrators
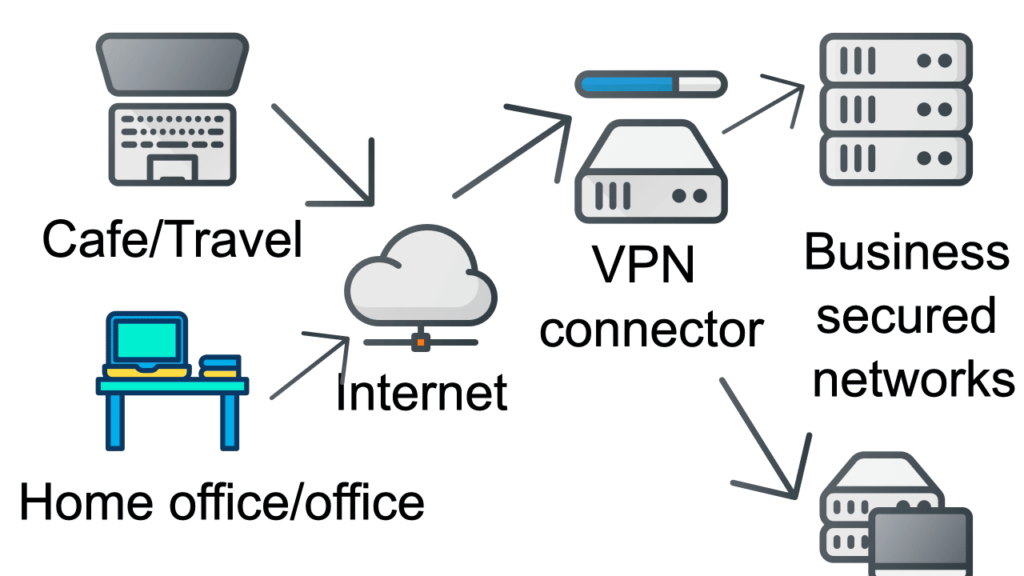
A Virtual Private Network (VPN) Concentrator serves as a potent networking device that allows multiple VPN connections to merge into a single network. Its role is similar to that of a VPN router, but it operates on a significantly larger scale. For organizations regularly employing traveling salespeople or employees, this is an ideal solution.
A VPN concentrator primarily works by establishing and configuring communication tunnels, authenticating users, allocating tunnel or IP addresses, encrypting and decrypting data, and ensuring end-to-end data transmission.
Moreover, it allows users to make a remote connection to a network and allows multiple users on one device to communicate with users on a different network. An added benefit is that a VPN concentrator can prevent Man-in-the-middle (MitM) attacks, where an attacker intercepts legitimate traffic and gains control over it.
Why You Should Consider a VPN Concentrator
Companies and organizations running numerous networked systems often find value in VPN concentrators. By connecting all these systems to a single VPN, they can protect their data from prying eyes, maintaining a high level of privacy.
Connections protected by VPN concentrators can range from a shared public network like the Internet to a dedicated private network like a leased telephone line.
Advantages of a VPN Concentrator
Here’s a rundown of some of the key benefits of using a VPN concentrator:
1. Secure Remote Access to the Company Network: With a VPN Concentrator, users can safely access the company network from anywhere globally with internet access. After the encryption process, the data and requests are sent to the business server via an encrypted tunnel, often established instantly upon a communication request’s initiation.
2. Instant Connection upon App Launch: Launching the app instantly builds a connection to the VPN concentrator, allowing immediate data reception.
3. Encrypted Connection for Security: Some apps can be configured to launch automatically upon powering the device, using a VPN concentrator to provide a secure connection to the company network.
4. Enhanced Router Capabilities: A VPN concentrator acts as a specialized router with a firewall and advanced protocols and algorithms.
VPN Concentrator, VPN Server, and VPN Router: What Sets Them Apart?
VPN concentrators, VPN servers, and VPN routers are distinct terms that often get confused. Let’s unravel their differences:
VPN Server vs. VPN Concentrator: While both encrypt data and network traffic, the VPN concentrator uses encrypted tunneling techniques to secure transmitted information. Essentially, it’s like a large VPN server. Additionally, VPN concentrators are typically used within corporate networks, particularly in large business networks with numerous remote workers.
VPN Concentrator vs. VPN Router: These two differ in terms of applications, background functionalities, and the extent of remote access. Depending on the specific router model, these differences can vary greatly. For medium to large companies, a VPN concentrator could be a valuable industrial solution. Conversely, a VPN router might be more suitable for small or medium-sized businesses due to its cost-effectiveness.
The Leading VPN Concentrator Brands
Several manufacturers offer VPN concentrators, with cost usually calculated based on the number of simultaneous VPN connections and the maximum throughput they can handle. A few prominent names in the industry include:
1. Cisco Meraki: Known for its ease of setup, Cisco Meraki’s VPN concentrators are well-suited for large corporations.
2. ShoreTel: ShoreTel’s VPN concentrators allow the establishment of secure IP telephony networks remotely, protecting your IP phones from unauthorized access.
3. HP: As a market leader in VPN concentrators, HP enables connecting your business system to users in different locations through their devices.
4. Aruba: Alongside HP, Aruba also holds a top spot in the Desktop/Laptop and Mobile categories, providing competitive VPN concentrator solutions.
Your Questions Answered
When is a VPN concentrator not necessary?
If a standard VPN suffices for your needs, a VPN concentrator might be unnecessary. For example, if you’re part of a large organization with many remote workers needing a connection to a single network, a standard VPN should do the trick.
Where should I install the VPN concentrator?
You should install a VPN concentrator on every device your telecommuting workers use.
What’s the typical price range for a VPN concentrator?
Typically, a VPN concentrator costs around $500. However, the price range can fluctuate between approximately $200 and $1,440, depending on specific features and capabilities.
Wrapping Up
The growing adoption of remote work has made corporate security a paramount concern. And VPN concentrators, as some of the most advanced security network equipment available, provide an answer. They offer a way to protect your organization’s data, communications, and remote workers, mitigating security threats in an increasingly interconnected world. Remember, understanding your organization’s unique needs will guide you toward making the best decision when considering VPN concentrators.




