Are you worried about the security of your online data? Are you looking for a way to protect your sensitive information? Well, look no further! AES-256-bit encryption could be the perfect solution for you.
In this blog post, we’ll explain what AES-256-bit encryption is and how it can help to keep your data secure.
Introduction to AES-256 Bit Encryption
AES-256-bit encryption is a type of symmetric encryption that uses a 256-bit key to convert plaintext into ciphertext and back. It is the most secure form of encryption to protect sensitive data such as financial information, medical records, and military communications.
AES-256-bit encryption is based on the Advanced Encryption Standard (AES) algorithm and was developed by the National Institute of Standards and Technology (NIST).
AES-256-bit encryption takes a plaintext message and runs it through an algorithm along with a secret key, producing an encrypted message. The secret key must be known to decrypt the message.
As long as the correct key is used, AES-256 will encrypt messages without the risk of being hacked or decrypted by brute-force attacks.
The main advantage of using AES-256 over other forms of encryption lies in its security level. It has been tested against various attacks and found virtually impenetrable due to its large key size.
Additionally, it’s faster than other methods since it only requires one round of processing for encrypting and decrypting data. This makes AES-256 ideal for applications where security and speed are important considerations, such as online banking or streaming video services.
Overall, AES-256-bit encryption provides a high data transmission security level while maintaining faster speeds than other methods. This makes it a popular choice for many organizations who need secure data transmission over the web or within their networks.
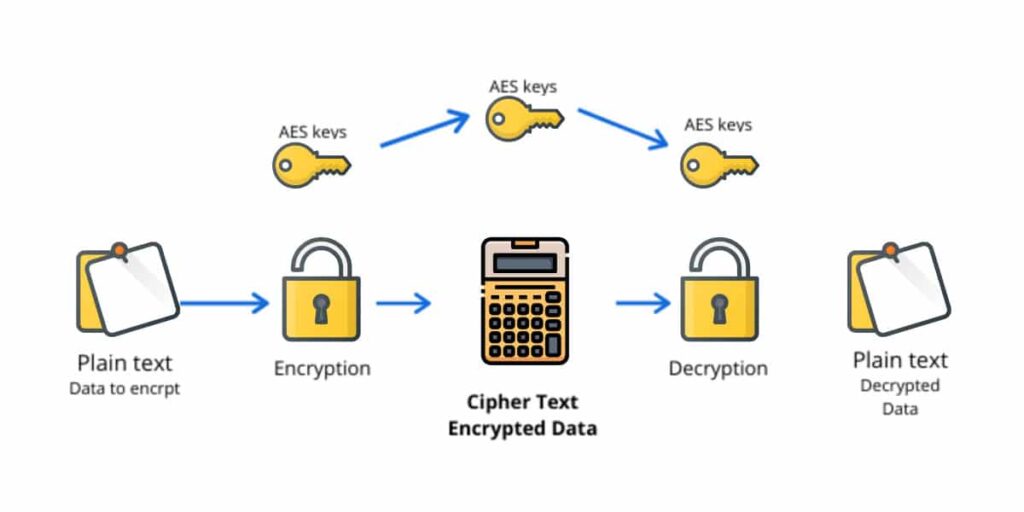
What Exactly Is AES?
AES is a widely used data encryption standard that is used all over the world. It is the federal standard used by the United States government, providing significant security and protection.
AES is a type of symmetric encryption that employs the same key to encrypt and decrypt data. To decrypt the data, both the sender and the receiver must use the same key. Symmetric encryption is faster than asymmetric encryption, but it is less secure.
What Does AES-256 Bit Encryption Offer?
AES-256-bit encryption is a symmetric encryption algorithm that protects data and information from unauthorized access. It employs a 256-bit key length to encrypt and decrypt blocks of messages, with each block containing 128 bits of data. AES-256-bit encryption is considered unbreakable by brute force due to its key size and the algorithm’s strength, making it one of the most secure encryption methods available.
The Advanced Encryption Standard (AES) was developed by the National Institute of Standards and Technology (NIST) in 2001 as a replacement for the Data Encryption Standard (DES). It offers AES’s different “flavors”: 128-bit, 192-bit, and 256-bit.
AES-256-bit encryption has been selected as the strongest method due to its incredibly high-security level. Moreover, AES-256-bit encryption is widely used in commercial cryptography software applications around the world due to its flexibility in terms of implementation.
When protecting your valuable data or information from unauthorized access or theft, AES 256-bit encryption should be your go-to choice for maximum security. The strength and complexity of this type of encryption make it practically impossible for hackers or crackers to break through, even with advanced techniques like brute force attacks.
Therefore, if you’re looking for an effective way to safeguard your sensitive information from prying eyes – whether personal or business-related – then AES 256-bit encryption should be on top of your list!
How Does AES-256 Bit Encryption Work?
When you encrypt your data with AES-256, the process begins by generating a unique 256-bit key based on mathematical algorithms. This key is then used to scramble the information so it cannot be deciphered without the right key.
Once the data is encrypted, it can only be decrypted by someone with access to the same 256-bit key. This means that even if an attacker could gain access to your encrypted data, they would not be able to decrypt it without the correct key. As such, AES-256 provides incredibly high security for your sensitive information.
AES-256 also uses various other cryptographic techniques to enhance its security further. These include message authentication codes (MACs) and digital signatures, which help verify that any changes made to encrypted files have not been tampered with or altered.
Overall, AES-256-bit encryption is one of the most secure forms of encryption available today and provides excellent protection for all kinds of sensitive data.
Is AES symmetric or asymmetric encryption?
AES is a symmetric encryption method since it utilizes only one key to encrypt and decode data, whereas asymmetric encryption needs both a public and a private key.
Because symmetric encryption uses just one secret key for encryption and decryption, AES-encrypted material cannot be read or understood if the key is unknown. AES-encrypted data can be read or understood if the key is discovered, even by hackers.
In layperson’s terms, the AES symmetric key is the technique that generates and decrypts ciphertext.
How secure is AES encryption?
AES encryption is one of the most secure encryption protocols available. It was selected by the National Institute of Standards and Technology as the standard for data encryption, and it has three “flavors”: 128-bit, 192-bit, and 256-bit.
AES-256 is considered practically unbreakable by brute force, as it would take billions of years to crack the key. Theoretically, AES has weaknesses, but it remains an incredibly safe protocol. Due to its flexibility and advanced data encryption standard, AES has become the most commonly used data protection standard worldwide.
The process of encryption involves a symmetric key that encrypts blocks of 128-bit, 192-bit, and 256-bit sizes. As long as users choose a strong key for their AES encryption system, their data will remain secure against any brute force attack.
Advantages of AES 256-Bit Encryption
AES 256-bit encryption is one of the most secure encryption methods available today. The strength of AES-256 comes from its key size, as it uses a 256-bit key length to encrypt and decrypt data. This makes AES-256 more robust against hacking attempts than other encryption methods, such as Data Encryption Standard (DES), which uses a 56-bit key length.
Also, it is open-source and relatively easy to understand and implement, making it very appealing to those who work with it. AES-256 also offers a high level of security due to its higher length key sizes (128, 192, and 256 bits). This encryption method is widely adopted by private organizations and governments worldwide, providing an additional layer of security for sensitive information.
Disadvantages of AES 256-bit encryption
AES-256-bit encryption is a widely used form of data security, but there are some potential drawbacks to consider. The primary disadvantage is that it requires a large key size of 256 bits, which increases the computational power needed for encryption and decryption.
Additionally, the key scheduling algorithm used in AES-256 must be properly implemented to prevent cryptanalytic attacks from occurring. Furthermore, AES-256 is more resource intensive than its 128-bit counterpart, resulting in slower performance and increased energy consumption. Finally, while AES-256 provides stronger security than 128-bit encryption algorithms, it may not be necessary for all data protection applications.
Choosing the Right Key Length
Choosing the right key length for data encryption is essential to ensuring its security. AES (Advanced Encryption Standard) is a popular symmetric encryption algorithm that uses different key lengths, including 128-bit, 192-bit, and 256-bit. The longer the key, the stronger the encryption and protection of data.
AES 128-bit encryption can be expressed as a 32-character hexadecimal string and requires 24 characters in base64. AES 256-bit requires a 256-bit long secret key which can be generated using a hashing algorithm if using a password or passphrase as the key. Of these two options, AES 256-bit is considered more secure since it offers the possible combinations of bits for an attacker to guess before gaining access to your data.
It’s important to note that choosing the right key length doesn’t guarantee absolute security; other factors, such as implementation flaws, weak passwords, or user negligence, can still threaten your data’s safety. Additionally, certain applications require specific keys; consult an expert or research to find out which type best suits your needs before investing in any encryption technology.
Limitations of the Advanced Encryption Standard
The Advanced Encryption Standard (AES) is an encryption algorithm that protects confidential information. It uses larger key sizes such as 128, 192, and 256 bits for encryption, making it more robust against hacking. However, this increased security comes with some limitations.
Firstly, the AES algorithm requires a secure way to share the encryption key with the other party for successful communication. Without a secure method of sharing the key, the data is vulnerable to attack and interception by malicious third parties.
Secondly, all three variants of AES (128-bit, 192-bit, and 256-bit) have different levels of security. The 128-bit version has less security than its larger counterparts due to its small key size, which can be cracked easily using brute force methods. Therefore if you are concerned about keeping your data safe from advanced hacking attempts, you should use at least 192-bit or preferably 256-bit encryption instead.
Finally, the larger variants of AES have limitations regarding the system resources required for encryption and decryption processes. The 256-bit variant requires 40% more system resources than its 192-bit counterpart, making it unsuitable for low-power devices or applications such as mobile phones or websites where speed and efficiency are important considerations.
Overall, AES is a powerful encryption algorithm that provides various levels of security depending on your requirements; however, it has some limitations in terms of system resources required for use and the need for secure methods to share keys between communicating parties.
Different Modes of Operation for AES encryption
AES (Advanced Encryption Standard) is a symmetric block cipher that encrypts electronic data. It has three key lengths – 128, 192, and 256 bits – which determine the algorithm’s level of security. To further ensure data security, AES also provides various Modes of Operation designed to provide confidentiality for different applications.
The Electronic Codebook (ECB) mode is the simplest and most basic mode of operation for AES encryption. In ECB, each plaintext block is encrypted using the same key, resulting in identical ciphertext blocks for identical plaintext blocks.
This makes it easy to implement, but it can be vulnerable to certain attacks like known-plaintext attacks or chosen-plaintext attacks, as there may be patterns in the encrypted data that could be exploited.
The Cipher Block Chaining (CBC) mode is more secure than ECB as it combines multiple blocks of plaintext with a unique initialization vector before they are encrypted using AES. Each block’s ciphertext output will depend on the previous block’s output, making CBC resistant against many types of attacks, such as replay attacks and known-plaintext attacks, since any change made to one block would affect all subsequent blocks.
The Counter Mode (CTR) is another popular AES mode that uses a counter instead of an initialization vector to encrypt each block independently from its preceding ones. This makes CTR highly parallelizable since encryption operations can happen simultaneously without waiting for other operations to complete.
Unlike CBC, CTR does not require padding, which means messages can be securely transmitted with varying lengths without compromising security or introducing potential vulnerabilities from unnecessary padding bytes.
Implementing and Using AES on Different Platforms
AES (Advanced Encryption Standard) is a powerful encryption algorithm that protects sensitive data on different platforms. AES provides three key lengths – 128-bit, 192-bit, and 256-bit – all designed to provide strong security while maintaining compatibility with existing hardware and software. The 256-bit key length has become the most popular choice for AES encryption due to its high-security level.
Implementing AES encryption can be done in several ways, depending on the platform or operating system used. For Windows systems, users can use BitLocker or other disk encryption tools such as TrueCrypt and VeraCrypt. FileVault 2 is available for full disk encryption using AES for Mac OS X systems. Linux systems also have several options for encrypting files and data using AES, including dm-crypt, encfs, and eCryptfs.
Using AES encryption on different platforms is relatively simple. Still, it’s important to remember that it should be implemented correctly to ensure maximum security and privacy of data stored on the system being encrypted. Each platform has specific instructions for correctly setting up and configuring an encrypted drive or partition, which must be followed carefully to prevent any data loss or accidental exposure of confidential information stored on the system.
Overall, implementing and using AES encryption on different platforms is fairly straightforward once you understand how each platform works and what measures need to be taken to keep your data safe from unauthorized access or malicious attacks.
With a little research into the various technologies available for each platform, you can easily configure your system with an effective layer of protection against hackers and other cyber threats without sacrificing performance or convenience.
Security Considerations with Using an Unsecure Network
Using an insecure network is a major security concern and can lead to serious consequences. Unsecure networks are networks that are not protected with any encryption or authentication measures. Without an encryption key, all communication over the network can be read by anyone who has access to it.
This means that confidential information such as credit card details, bank account numbers, and personal data can be easily accessed by malicious actors, resulting in identity theft and financial loss. Also, malicious actors can use these networks to launch attacks on other systems connected to the network.
Taking certain security measures to protect yourself from these risks when using an insecure network is important. One of the most important security steps is to use a Virtual Private Network (VPN) for all communication over the unsecured network.
A VPN encrypts all data sent over the internet so that it cannot be read by anyone who does not have access to your private encryption key. Additionally, you should avoid downloading files from unknown sources or clicking on links sent via email or text message, as this could lead to malicious software being installed on your computer without your knowledge.
Finally, ensure that you keep your antivirus software up-to-date so that any malicious software is detected before it can cause any damage.
Best Practices for Data Protection and Security
Data protection and security are essential for businesses of all sizes. It is important to ensure that sensitive customer information, financial data, and other private data remain secure.
One of the best data protection and security practices is using a reliable encryption system such as the Advanced Encryption Standard (AES). AES is a symmetric block cipher that encrypts and decrypts data in blocks of 128 bits by using cryptographic keys.
AES comes in three different sizes: 256-bit AES, 192-bit AES, and 128-bit AES; the largest size, 256-bit AES, is the most secure. The federal government uses this encryption system, and it has become the industry standard for data security.
Another best practice for protecting your data is to use strong passwords that include upper case letters, lower case letters, numbers, punctuation marks, and special characters. Your passwords should also be changed regularly to prevent unauthorized access to your accounts or systems. Additionally, you should avoid using public Wi-Fi networks when handling sensitive information, as they can be easily compromised.
Finally, it’s important to back up your data regularly to ensure you have copies of any important documents or information stored safely in case something happens to your original files or systems. You should also consider implementing two-factor authentication processes so that an additional code or token must be entered each time a user attempts to log into an account or system.
By following these best practices for data protection and security, you can help keep your business safe from cyber threats and breaches while ensuring that valuable customer information remains secure at all times.
Potential Vulnerabilities with using AES 256-bit encryption
AES-256 is an encryption standard approved by the US government to protect data from unauthorized access. It uses a 256-bit key length to encrypt and decrypt messages, divided into 128-bit blocks. Despite its high level of security, AES-256 is still vulnerable to certain types of attacks.
One type of attack against AES-256 is called a “related-key attack.” This attack exploits poorly implemented algorithms and requires fewer resources than brute force attacks, making it easier for attackers to break into systems.
Another vulnerability with AES-256 is that it can be subject to brute force attacks if precautions are not taken. For example, if an app uses AES-256 instead of AES-128, it could drain battery life quickly as attackers try different keys to gain access.
While there have been some minor cracks in the security of AES 256-bit encryption, it remains one of the most secure encryption standards available today. It would take billions of years for someone to crack through the current technology using a brute force attack, making it almost impossible for anyone without access to highly sophisticated resources or tools to penetrate a system using this encryption standard.
Practical Applications of the Advanced Encryption Standard
The Advanced Encryption Standard (AES) is a widely-used encryption standard that uses a symmetric key to protect data from unauthorized access. AES is the first and only publicly accessible encryption protocol approved by the US National Security Agency (NSA) for protecting sensitive information.
AES can be used in various applications to secure data confidentiality, integrity, and authentication. Its 128/192/256 bits key size encrypts data in blocks of 128 bits each. This makes it virtually impossible for attackers to decrypt the data without knowing the correct key.
In practical terms, AES can secure online transactions like banking and e-commerce by encrypting sensitive user information, including passwords or credit card numbers. It also protects digital communications, such as emails or text messages, from being intercepted or stolen by an unauthorized party. Additionally, many software systems use AES as an extra layer of security when storing files on computers or cloud-based storage services so that only authorized users can access them.
Apart from these applications, AES is also used increasingly in embedded devices such as smartphones or wireless routers. It helps protect against threats like malware infections or malicious attacks while still allowing users access to their device’s features and functions. The increasing prevalence of IoT devices has made AES even more important. It helps secure these devices from potential cyber threats and ensures their safety for all users who depend on them for everyday tasks.
Overall, AES provides robust protection against various types of cyber threats with its high security and reliability, making it one of the most trusted encryption protocols available today.
Conclusion
AES-256, or Advanced Encryption Standard, is an encryption protocol widely used to protect data and information from unauthorized access. It is a symmetric encryption algorithm that uses a 256-bit key length for increased security. It also uses the SPN (Substitution-Permutation Network), which allows for more secure data encryption.
This makes AES-256 one of the most secure means of protecting data and sensitive information from cyber-attacks and other malicious activities. AES-256 is especially recommended for government cybersecurity, encryption, and electronic data transmission applications where high security is essential.




